Network Access Control Diagram
Traveling mind: advanced access control market Pin on network How to wire your door access control system
How Does Network Access Control Work? – Isotropic Networks®, Inc
Network access control Sue best security solutions Network security diagrams solution
6-network access control
Control network access device authentication nac system identity security user juniper using software directory active networksControlled access in computer networks / pin on computer and networks Network access control solutionsOverview of poe access control systems.
Security network diagram control diagrams devices computer access networks solution model secure examples cloud conceptdraw encryption solutions area system softwareAccess control security configuration software click solution attendance hardware time operation sue solutions note enlarge Controlled access in computer networks / pin on computer and networksAccess control system hardware acs security single software type standalone multi telecom solution networking information desired locally remotely premises monitor.
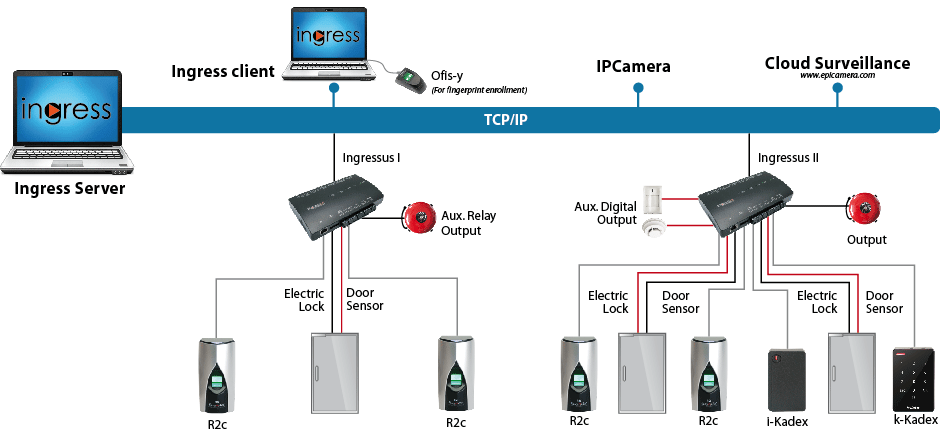
Access control general architecture
Unified enterprise access control :: various access control systemsEnterprise access control and time & attendance software Control network access using device identity authenticationAccess network control works.
Network access control vs software defined perimeter – or bothPoe overview traditional Access control systems architecture system general security components acs physical controls building io facility overview technology elementsNetwork access control.

Network access control nac security system intranet development into blogs agent health client however if
Software educbaResearch on unified network access control architecture Ip based access control systemsNetwork access control.
The network access control architecture.Access network flow diagram Alchetron networksControl access topology fingertec centralized ip advanced market controller diagram gif.

Eee world, department of eee, adbu: basic installation of access
Access control system acs architecture networking telecom solution square typicalEee adbu rfid electronicsforu Network access controlAccess controller,network tcp/ip access control panel board reader for.
Attendance enterprise idzone هندسه نظامAccess control network controller board reader tcp ip panel wiegand door use s4a Access controlHow does network access control work? – isotropic networks®, inc.

Access control system overview
Access control system (acs) ~ b square telecom networking solutionAccess control network software defined vs perimeter What network access security method involves the analysis of a physicalAccess control system with all type of hardware and software solution.
Access control system diagram ip topology systems controller english using scheier 2006 simple writework technologyNetwork security basics: access control lists Access control system network ip payroll nairaland remote time technology based market sysAccess control diagram door system wire doors kintronics.

Wired & wireless networking • building a well-thought-out network
What is network access control?Ip access control system Network access control security training skillset.
.
.png)

Overview of PoE Access Control Systems | FS Community

Enterprise Access Control and Time & Attendance Software - IDCUBE

How Does Network Access Control Work? – Isotropic Networks®, Inc

Research on Unified Network Access Control Architecture | Semantic Scholar

Control Network Access Using Device Identity Authentication

What is Network Access Control?